Mirrored Padding
Mirrored Padding
Easy:
Imagine you have a box of toys that you want to keep safe so they don’t get broken when you move them around. But sometimes, when you carry the box, it tips over because the toys inside aren’t evenly distributed.
To solve this problem, you could take some toys from one side of the box and put them on the other side, making sure there’s an equal number of toys on both sides. This way, no matter how you carry the box, it won’t tip over because the weight is balanced.
Mirrored padding in computers works like balancing the toys in the box. When we send information over the internet or save it on our computer, we often need to make sure it doesn’t get mixed up or damaged. Just like balancing the toys, we can use mirrored padding to protect the information.
Here’s how it works: Imagine you have a secret message that you want to send to your friend. Before sending it, you write down the message, then copy it exactly as it is onto a new piece of paper. Now, you have two identical copies of the same message. You send one copy through the internet and keep the other one safe at home.
When your friend receives the message, they do something special with it. They compare the message they received with the exact copy you kept at home. If everything matches perfectly, they know the message was delivered safely without any mistakes or damage.
This method of using two identical copies (mirroring) helps ensure that the information stays safe and unchanged during its journey from one place to another, just like how having an equal number of toys on both sides of the box keeps it from tipping over.

Moderate:
Mirrored padding is a technique used in data transmission and storage to ensure the integrity and security of digital information. It involves adding extra bits to the original data before transmitting or storing it, creating a mirror image of the original data. This process serves multiple purposes:
- Error Detection: By comparing the original data with the received data after transmission or storage, mirrored padding allows for the detection of errors that may occur during these processes. If even a single bit changes due to noise or interference, the comparison will reveal discrepancies, indicating that the data has been altered or corrupted.
- Data Integrity Verification: The mirroring ensures that the data remains intact and unaltered throughout its journey from sender to receiver or during storage. Any modification, intentional or accidental, will result in a mismatch between the original and the mirrored data, signaling a breach in integrity.
- Security Enhancement: In cryptographic applications, mirrored padding can enhance security by ensuring that any tampering with the data can be easily detected. This is particularly useful in scenarios where data confidentiality and authenticity are critical.
How Does It Work?
Let’s break down the process with a simple example:
Suppose we have a binary string `1011` (which represents our data) and we decide to add mirrored padding to it. Here’s how we might do it:
- Original Data: `1011`
- Mirrored Padding: We append a copy of the original data to itself. So, `1011` becomes `10111011`.
Now, if we were to transmit or store this padded data (`10111011`) and later retrieve it, we would compare it with the original unpadded data (`1011`). If the received data exactly matches the original data plus the mirrored padding (`10111011`), we can be confident that the data has remained intact and untampered.
Practical Applications
- Network Communications: Mirrored padding is used in protocols like TCP (Transmission Control Protocol) to detect and correct errors in transmitted data packets.
- Storage Devices: Hard drives and SSDs use error correction codes, which include concepts similar to mirrored padding, to ensure data integrity during read/write operations.
- Cryptography: In cryptographic algorithms, mirrored padding (or variations thereof) is employed to safeguard against unauthorized modifications to encrypted data.
In summary, mirrored padding is a fundamental technique in data processing and security, ensuring that digital information remains accurate, secure, and untampered during its lifecycle.
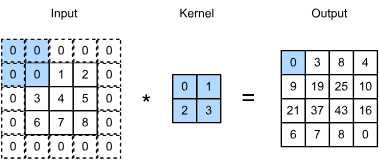
Hard:
Mirrored padding is a technique used in image processing where the edges of an image are extended by reflecting the image’s edge pixels. This creates a seamless transition at the borders, which can be useful for various tasks such as convolution in neural networks, where maintaining the context of edge pixels is important.
Here’s a more detailed explanation:
What is Mirrored Padding?
- Padding: Adding extra pixels around the edges of an image.
- Mirrored Padding: Instead of adding blank or constant-color pixels, you extend the image by mirroring the pixels at the edges.
How It Works
Imagine you have a small image and you want to add a border around it using mirrored padding:
- Original Image:
```
A B C
D E F
G H I
```
Here, `A` to `I` are the pixels of the image. - Mirrored Padding: You add extra rows and columns around this image by reflecting the edges:
```
E D E F E
B A B C B
E D E F E
H G H I H
E D E F E
```
- The top and bottom rows are created by mirroring the second and second-last rows.
- The left and right columns are created by mirroring the second and second-last columns.
Why Use Mirrored Padding?
- Smooth Edges: It helps in maintaining smooth and continuous edges when processing the image, preventing abrupt transitions.
- Context Preservation: In convolution operations, it ensures that the filters have meaningful data to process at the borders, as the mirrored pixels provide context similar to the original image.
Visual Example
Imagine your image is a photo of a beach, and you want to add mirrored padding around it:
- Original Edge:
```
[Beach]
``` - Mirrored Padding:
```
[Sea][Beach][Sea]
[Sand][Beach][Sand]
```
If the left side of the beach photo shows the sea and the right side shows the sand, mirrored padding would extend the image with the sea on the left and sand on the right, creating a reflection-like effect.
Mirrored padding is useful in many applications, such as image recognition, where maintaining the integrity of the image edges is crucial for accurate analysis.
Comments
Post a Comment